Microsoft Defender for Cloud Apps
Moving to the cloud increases flexibility for employees and IT alike. However, it also introduces new challenges and complexities for keeping your organization secure. To get the full benefit of Cloud Apps and services, the IT team must find the right balance of supporting access while maintaining control to protect critical data.
Microsoft Cloud App Security is a Cloud Access Security Broker (CASB) that supports various deployment modes including log collection, API connectors, and reverse proxy. It provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyber threats across all your Microsoft and third-party cloud services.
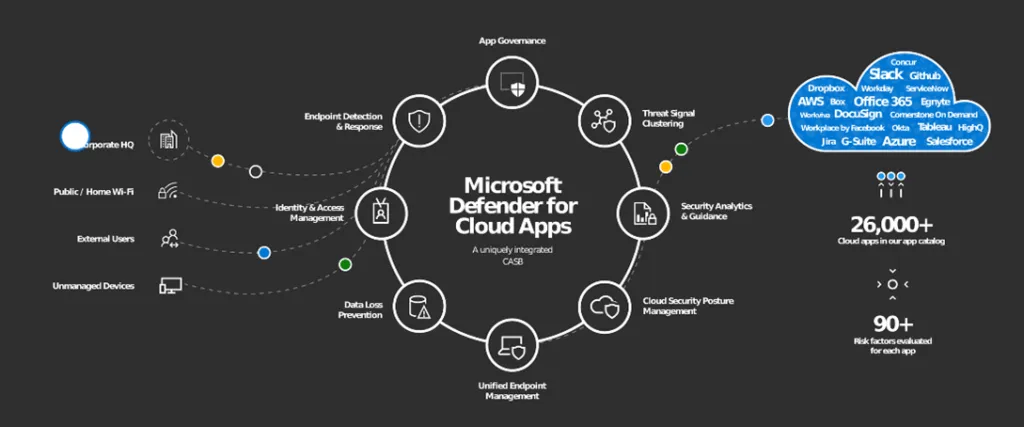
About the architecture
Microsoft Defender for Cloud Apps is natively integrated with leading Microsoft solutions. It is designed with security professionals in mind.
At the core, the Microsoft Defender for Cloud Apps is a state-of-the-art concept of native integrations to provide a simple deployment experience, centralized management, and innovative automation capabilities—while still allowing you to integrate non-Microsoft solutions from your existing environment, such as SIEM or Secure Web Gateway.
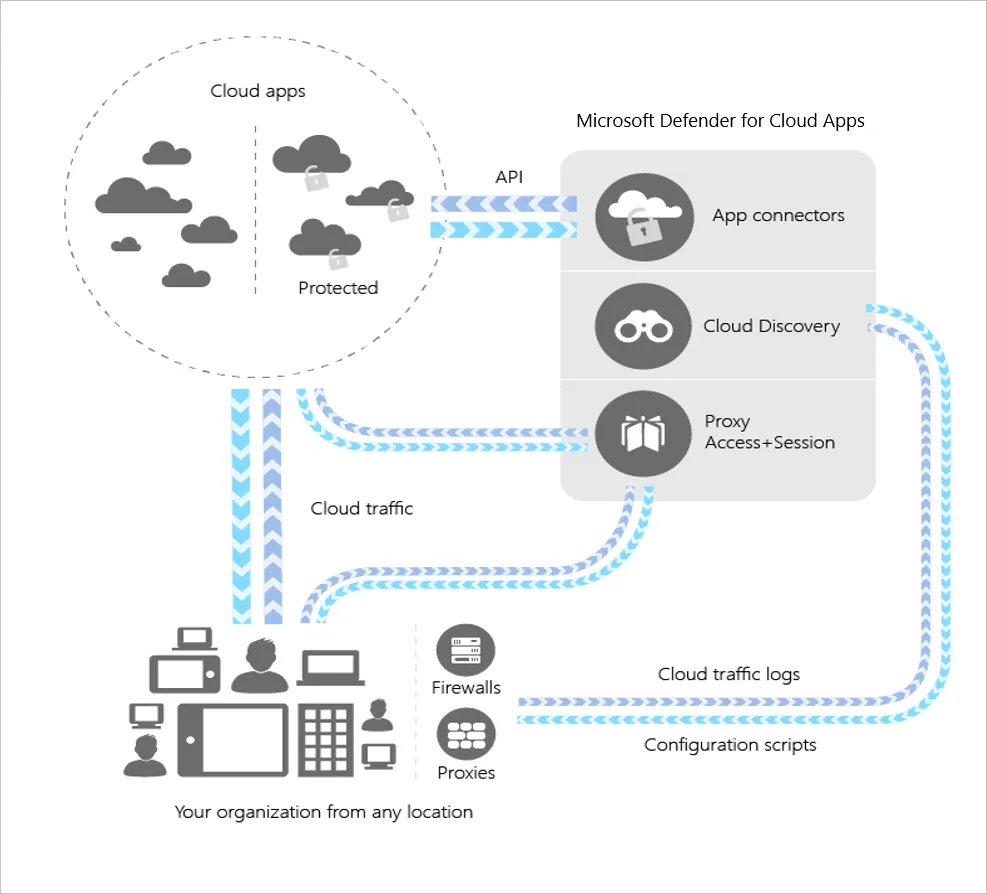
Learn About User-Case Scenarios
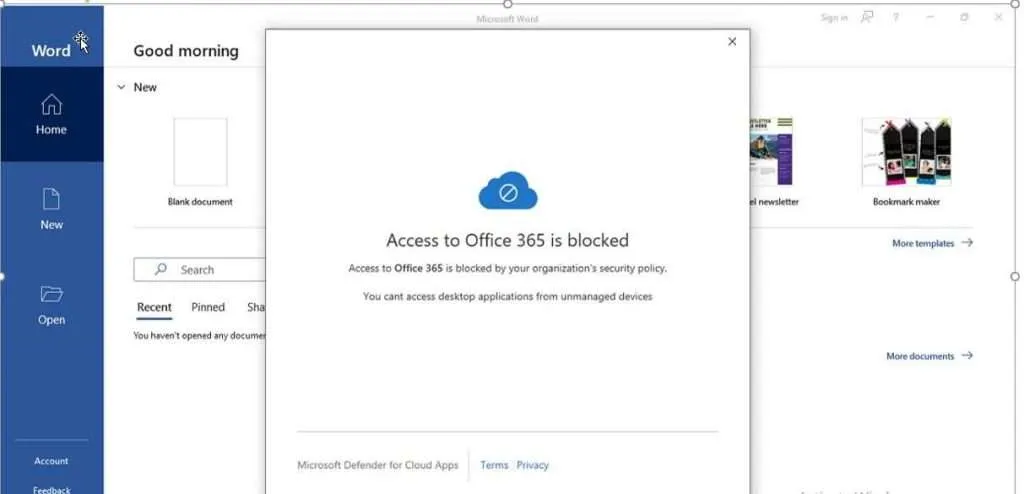
Use-case #1: Block access from desktop app
Defender for Cloud Apps enables to block desktop applications from unmanaged or specific devices or users.
Some users may try to use non-corporate computers to access company information. It happens that they use corporate accounts on these devices, which generates a certain risk. When there is an ongoing session in applications, such as Offices or Teams, a person could access sensitive information. In addition, it could accidentally register that device in the company’s Azure AD, which will generate inconveniences for that device. To this end, it is necessary to block the use of desktop applications from unmanaged devices.
This configuration suits the medical industry, law firms, education, and many others.
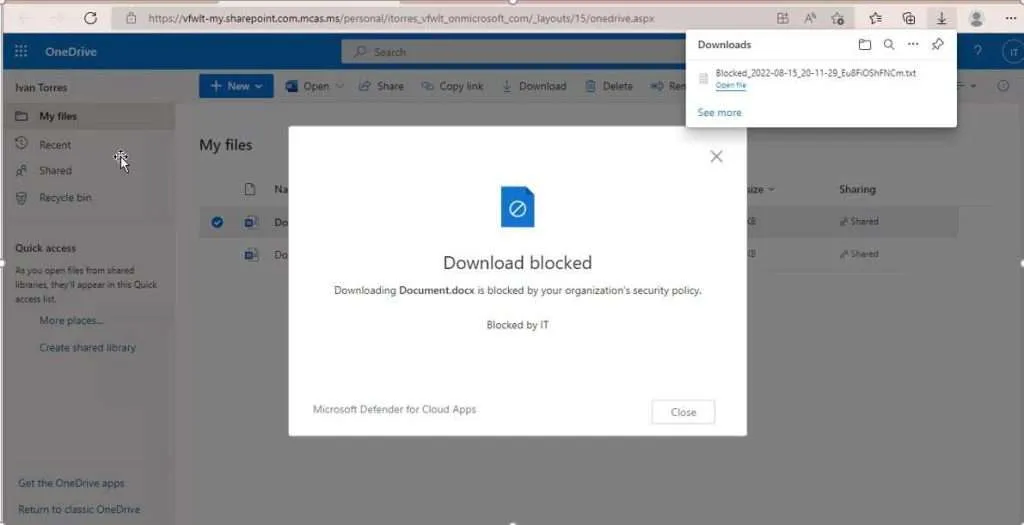
Use-case #2: Block downloads
Defender for Cloud Apps enables to block downloads from unmanaged devices. Moreover, it will evaluate the content of files being downloaded and will block any violations in real-time.
You can restrict the download of attached files for your guest users by adding an extra layer of security for users outside the company who access any company data.
By enabling this setting, you can prevent a company user from downloading sensitive information on a non-company device this will mitigate leaked information.
Example: Some users share information with external consultants. Imagine, if one of your coworkers downloads sensitive information on a borrowed device. After, by mistake, the left data turns out to be out of your control. This can put at risk any corporate information.
This configuration suits the medical industry, law firms, education, and many others.
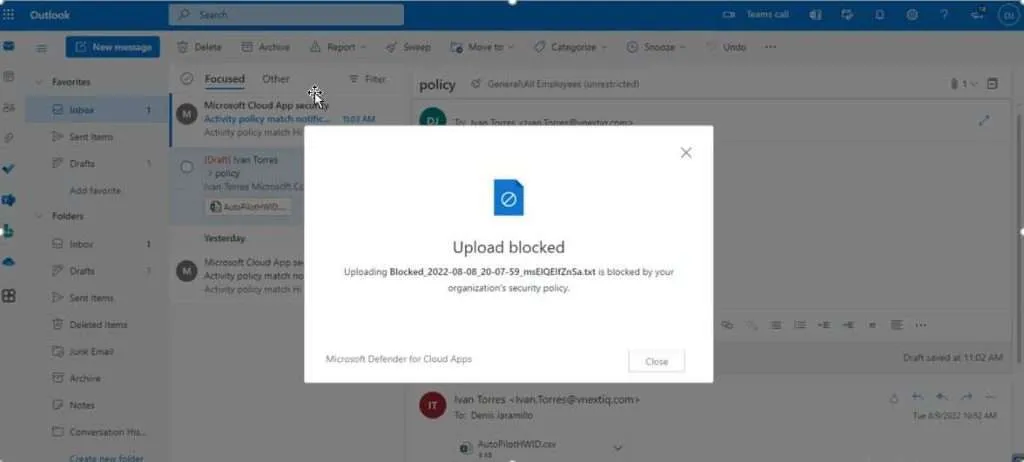
Use-case #3: Upload blocked
File upload is necessary for any industry, however, unrestricted uploads raise an exposure to surface cybercriminals or human errors. You can block this setting only for unmanaged devices, or specific groups. Some of the issues that you can manage by enabling this setting are:
Prevent overwriting files
Control upload of very large files
Prevent malicious content
Prevent file metadata vulnerabilities
Example: You are sharing with your guest users some corporate data through Microsoft Teams. One of the guest users uploads and replaces an old version of a critical file by mistake, so some decisions were taken based on that file causing disruption and business risks.
This configuration suits the medical industry, law firms, and many others.
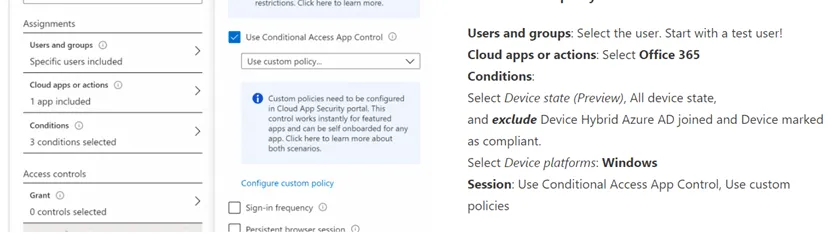
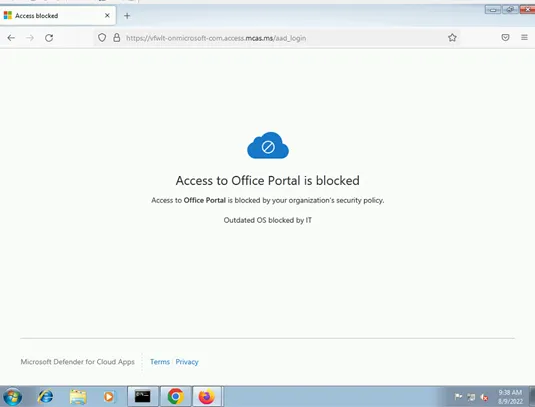
Use-case #4: Block Office access for outdated OS Access
It is likely that some of your users still use Windows 7 on their home computers, or any other outdated operating systems. Bearing that in mind, you can still block access from those OS.
Outdated software doesn’t just leave your security vulnerable to human malice. It can also become more exposed to system failures or cyber-attacks.
If a device stops working or becomes affected, it can stop you in your tracks. Therefore, while waiting for the outdated software to work, you could loose any data that’s stored on the outdated system.
Here are some of the issues that you can manage by enabling this setting:
Reduce cyber-attack surface
Reduced user experience caused by software bugs
Incompatibility with some office 365 features
Loss of data caused by software failures
Example: Some users can use an old laptop to access corporate data. This device can be affected by malware or some vulnerability reported. In this case, Windows update can become a solution. If this device was used to access the internal network or corporate data, it could put the business at risk by exposing it to system failure and vulnerable to cyber attacks.
This configuration suits the medical industry, law firms, education, and many others.
Use-case #5: Alert for sharing externally
Unauthenticated sharing (Anyone links) can be convenient and useful in various scenarios. Anyone links are the easiest to share. People can open the link without authentication and are free to pass it on to others.
To date, most administrators do not have a way to identify what information is shared or what corporate domains are being shared.
By configuring these features, you could receive an alert if any user shares information externally which would help in preventing data leakage.
Example: A user decides to share information with an external consultant, however, he doesn’t take the precaution of sharing only with that person, and by mistake, the access link is established as unauthenticated. Any person with that link would have access to the information and there is no way to identify this type of situation. The only solution would be using Defender for Cloud Apps.
This configuration suits the medical industry, law firms, education, and many others ones.
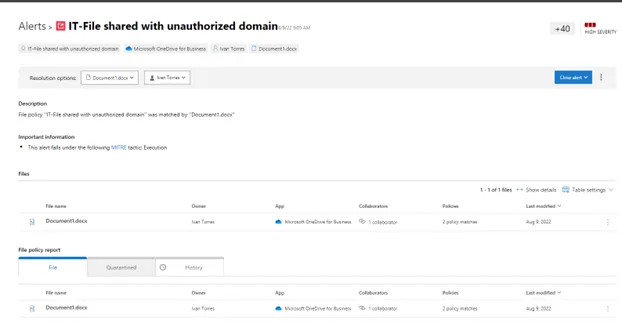
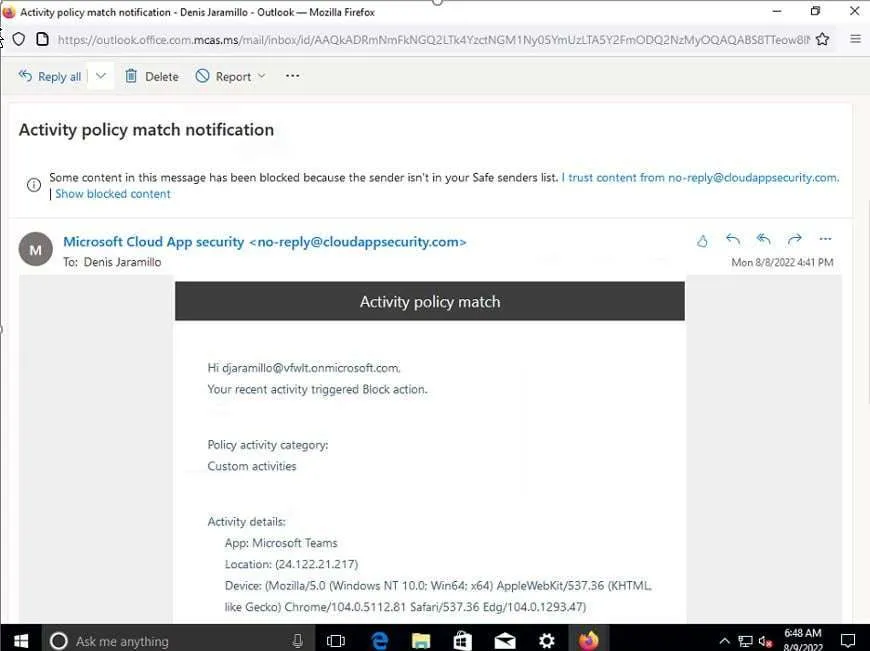
Use-case #6: Outdated Browser
The outdated web browser often leads to security threats that can cause your browser to compromise both information and data.
When an user uses an outdated browser via an unmanaged device. It can cause compatibility issues, lack of new features and low performance. However, the most important thing drawback – it can result in compromising password.
All the browsers will have bugs; none are free of vulnerabilities. To this end, developers are quick to patch these issues and release the fix in the next update.
Example: One of your corporate users use a borrowed device to access internal resources, unfortunately the device had an outdated browser with unpatched vulnerabilities, user’s credentials were compromised due to this situation
This configuration suits the medical industry, law firms, education, and many others.
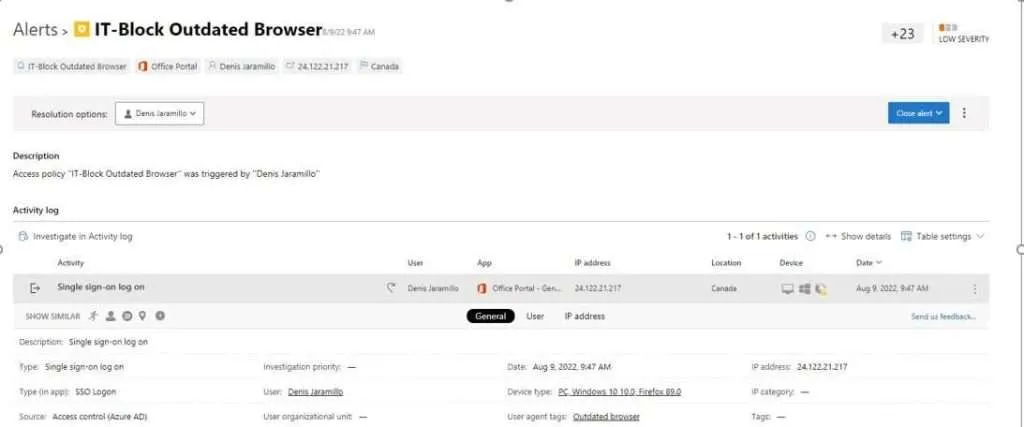
Use-case #7: Tor as anonymous networks
At a high level, when you connect to Tor, your computer becomes a node. Therefore, it can be used by any other Tor users to relay their traffic.
The Tor network hides your identity by moving your traffic (that was encrypted) across different computers, or nodes, located across the world. Instead of taking a direct route from source to destination, the data packet sent on the Tor network takes a random pathway through several servers that cover your tracks.
Criminals use these networks to gather information, and attack the business infrastructure by:
- Exposing the organization to malware and botnet attacks
- Exposing the organization to DDoS attacks
- Enabling employees to bypass security controls
- Information theft
This configuration suits the medical industry, law firms, education, and many others.
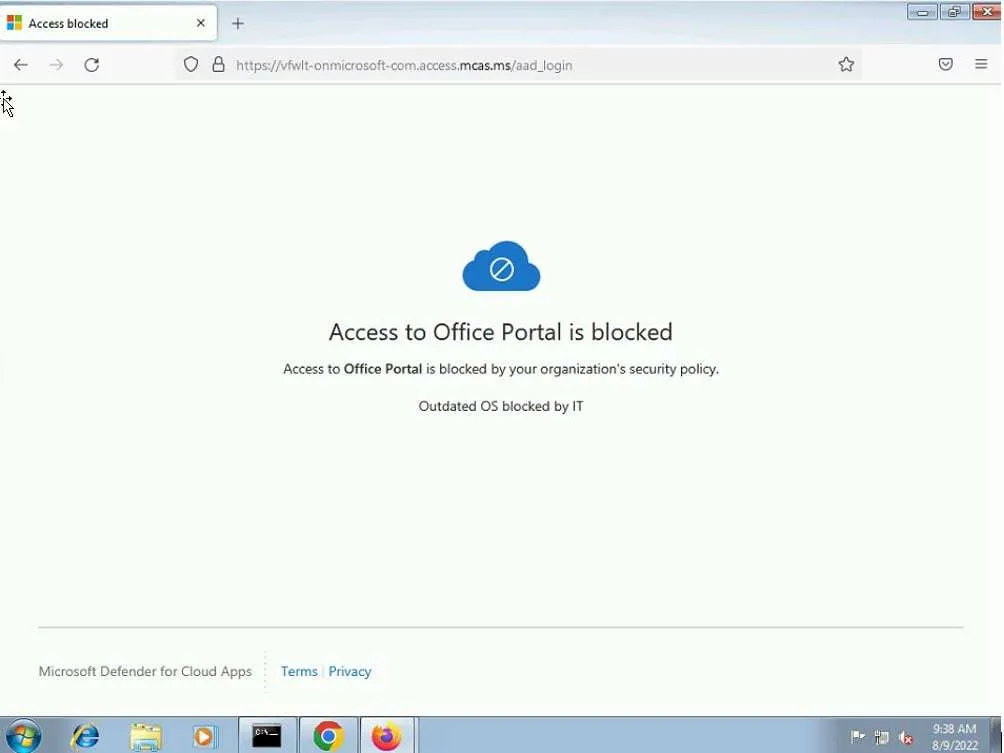
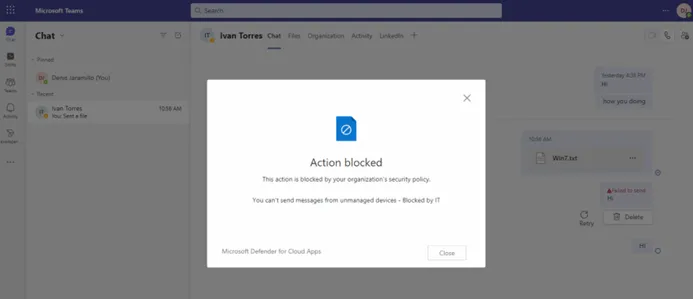
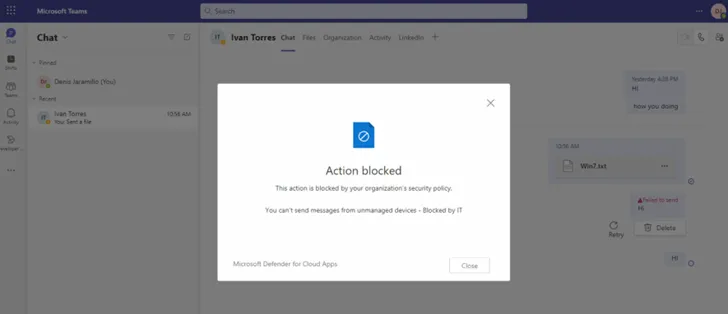
Use-case #8: Block send messages from unmanaged devices
Frequently, due security reasons you need to control messages flow from Microsoft Teams for specific device group or users.
Businesses and consumers are looking to leverage video conferencing, collaboration, document sharing and instant messaging features from these tools. However, they can represent security risks and threats, as they are used as a vehicle to access to internal and sensitive/confidential data.
Example: Guest devices are not managed by the organization. Therefore, the status of the device is unknown. The risk exists that unmanaged devices (either from guests or unmanaged devices of internal users) may contain malware, or malicious files that may be uploaded to Teams channels or sent as chat message.
This configuration suits the medical industry, law firms, education, and many others.
To sum up, all the enlisted Cloud App user-cases are chosen based on the frequency and relevancy in diverse business industries. Our consultants have always been providing the most beneficial approaches to overcome potential security issues and risks with the solutions that can best meet your business needs.
Defender for Cloud Apps is defined as valuable asset to avoid “blocks”, “alerts”, “violations” occurring depending on your particular scenario. Reach out to VNEXT experts here to support you during the process to secure your organization.
